AWS Roles
AWS-Roles in Amorphic used to switch to the AWS console from Amorphic. This feature helps the users to view their resources in AWS.
In amorphic we have some pre-defined system generated Aws-Roles. User can have multiple AWS-Roles attached and has the ability to switch to AWS console using these roles. In AWS console, these Roles only have View Permissions.
Once the AWS-Role is attached to a user, user will be able to see that Role in the Switch To Console option in Profile icon, which they can use to switch to AWS console.
What is an AWS-Role?
These are Roles created by Amorphic in AWS, which used to switch to AWS-Console from Amorphic.
AWS-Roles has the following properties:
- An AWS-Role can have multiple users attached to it.
- A System generated AWS-Role only have view permissions in AWS console and these can't be deleted.
- With v2.0 users can have custom AWS roles which helps them to switch to AWS console with set of permissions defined by them.
In Amorphic we have three types of system AWS-Roles:
- DMS View Role : System generated AWS-Role with view only permissions for DMS service.
- Glue View Role : System generated AWS-Role with view only permissions for Glue service.
- All System View Role : System generated AWS-Role with view only permissions for All AWS services which are part of Amorphic.
DMS View Role
This AWS-Role only have view permissions of DMS service in AWS. Once the user switch to AWS console using this Role, user will be able to see resources in DMS and its logs from a particular log group of cloudwatch.
Log groups that are part of this AWS-Role:
- log-group:/...replicationTaskCreation
- log-group:/...connections
Glue View Role
This AWS-Role only have view permissions of Glue service in AWS. Once the user switch to AWS console using this Role, user will be able to see all resources associated with the Glue service and its logs from a particular log group of cloudwatch.
Log groups that are part of this AWS-Role:
- log-group:/aws-glue/jobs/error
- log-group:/aws-glue/jobs/logs-v2
- log-group:/aws-glue/jobs/output
All System View Role
This AWS-Role only have view permissions of AWS services that are supported by Amorphic. Once the user switch to AWS console using this Role, user will be able to see resources of all AWS services which are part of Amorphic.
For now, list of AWS Services supported by All System View role:
- Amazon Athena
- Amazon Comprehend
- Amazon Comprehend Medical
- AWS Database Migration Service(DMS)
- Amazon DynamoDB
- Amazon Forecast
- AWS Glue
- Amazon Kendra
- Amazon Kinesis
- Amazon Kinesis Data Analytics
- Amazon Kinesis Data Firehose
- AWS Lake Formation
- Amazon RDS
- Amazon Redshift
- Amazon Rekognition
- Amazon SageMaker
- AWS Step Function
- Amazon Textract
- Amazon Transcribe
- Amazon Translate
AWS-Role Metadata Information
| Type | Description |
|---|---|
| Role Name | Role Name, which uniquely identifies the functionality of the role. |
| Role Description | A brief explanation of the aws-role typically the functionality for what it is used. |
| Consolidated AWS Permissions | Permission is an action defined for a particular AWS service. Each aws-role consists of a group of permissions. These permissions determines the level of access within AWS. |
| UsersAttached | The list of users to whom the role is attached. |
| CreatedBy | Who created the role. |
| LastModifiedBy | Who has recently updated the role. |
| LastModifiedTime | Timestamp when the role was recently updated. |
Role Operations
Amorphic allow some operations on the AWS-Roles.
- View Role : View existing
Role Metadata Information. - Update Role : Update users attached on existing AWS-Roles.
- Switch To Console : This functionality helps user to switch to AWS console using these AWS-Roles.
View Role

If the user has sufficient permissions to view an aws role, He/She can view all the Role informations by clicking on the Role Name under the AWS-Roles section inside Management Menu.
Update Role
If the user have sufficient permissions, He/She can update details about an AWS Role by selecting the AWS Role Name under the AWS-Roles section inside Management Menu. This will re-direct to a different page where you see details about the AWS Role and from this page you can choose Edit Role button and select the users needs to be attached to role and finally clicking Update.
Switch To Console
Switch To Console functionality is enabled for users who have an AWS-Role attached to. This functionality can be accessed by clicking on the User Profile icon and Switch To Console item of the the drop down menu. Users will be presented with a drop down list of AWS-Roles that He/She is attached to, and selecting one of the role will switch to AWS console automatically.
Custom AWS Roles
With v2.0 release we introduced custom AWS Role support in Amorphic. This feature allows users to switch to AWS console with the IAM policy that defined by them. To use this feature customer need to contact Cloudwick support team and provide a valid IAM policy document.
The IAM policy document must be a valid JSON policy in text file with .txt extension. Policy document filename must start with an alphabet and can contain - & alphanumeric characters only.
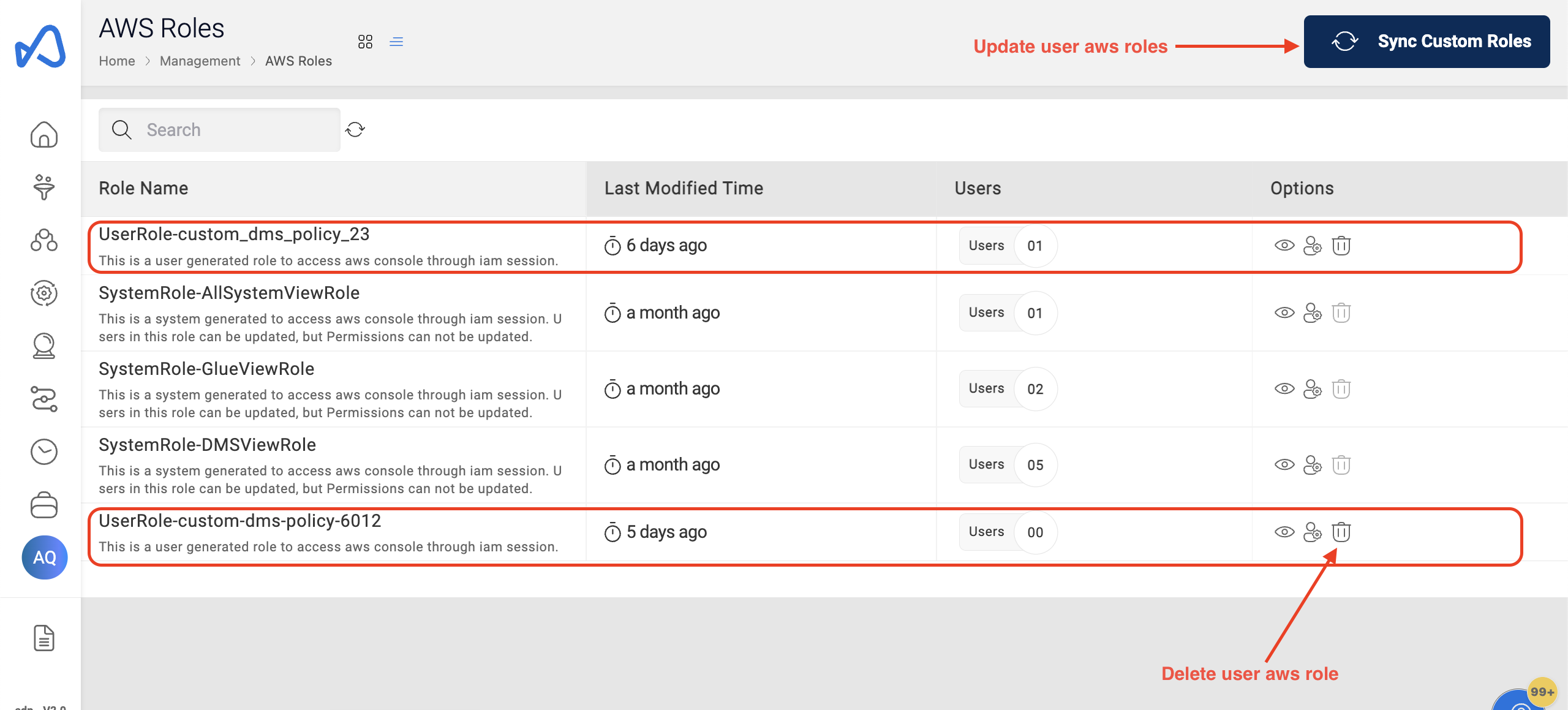
Cloudwick support team will upload IAM policy document to S3 after reviewing and the custom AWS role generation can be trigger from Amorphic directly by clicking Sync Custom Roles button in the AWS Roles section.
After the successful generation of custom AWS roles, users will be able to see the custom roles in the AWS Roles section inside Management menu. The custom AWS role names will be in the format UserRole- followed by the filename given by the customer.
User have the option to update the IAM permissions in these custom AWS roles. Inorder to do that, after successful upload of the policy document by Cloudwick support team, trigger the custom role update process by clicking the same Sync Custom Roles button in the AWS Roles section. Users will get email about the details of the create/update process after create/update process is completed, if they've enabled email subscription.
Users with the right permissions can delete these custom AWS roles from Amorphic, only if no other users are attached to those roles.
Below images shows the User AWS roles and its operations: