AWS Roles
AWS Roles is a feature in Amazon Web Services (AWS) that allows an administrator to control access to specific resources and actions within AWS for different users or groups. The Amorphic team can set up custom roles for customers based on their needs.
AWS-Roles in Amorphic used to switch to the AWS console from Amorphic. This feature helps the users to view their resources in AWS.
In amorphic we have some pre-defined system generated Aws-Roles. You can have multiple AWS-Roles attached and has the ability to switch to AWS console using these roles. In AWS console, these Roles only have View Permissions.
Types of System AWS-Roles
These are Roles created by Amorphic in AWS.
In Amorphic we have three types of system AWS-Roles:
- DMS View Role : System generated AWS-Role with view only permissions for DMS service.
- Glue View Role : System generated AWS-Role with view only permissions for Glue service.
- All System View Role : System generated AWS-Role with view only permissions for All AWS services which are part of Amorphic.
AWS-Roles has the following properties:
- An AWS-Role can have multiple users attached to it.
- A System generated AWS-Role only have view permissions in AWS console and these can't be deleted.
- With v2.0 users can have custom AWS roles which helps them to switch to AWS console with set of permissions defined by them.
DMS View Role
DMS view role only has view permissions of DMS service in AWS. Once you switch to AWS console using this Role, you will see resources in DMS and its logs from a particular log group of cloudwatch.
Log groups that are part of this AWS-Role:
- log-group:/...replicationTaskCreation
- log-group:/...connections
Glue View Role
Glue view role only has view permissions of glue service in AWS. Once you switch to AWS console using this Role, you will see all resources associated with the Glue service and its logs from a particular log group of cloudwatch.
Log groups that are part of this AWS-Role:
- log-group:/aws-glue/jobs/error
- log-group:/aws-glue/jobs/logs-v2
- log-group:/aws-glue/jobs/output
All System View Role
This AWS-Role only have view permissions of AWS services that are supported by Amorphic. Once the user switch to AWS console using this Role, user will be able to see resources of all AWS services which are part of Amorphic.
For now, list of AWS Services supported by All System View role:
- Amazon Athena
- Amazon Comprehend
- Amazon Comprehend Medical
- AWS Database Migration Service(DMS)
- Amazon DynamoDB
- Amazon Forecast
- AWS Glue
- Amazon Kendra
- Amazon Kinesis
- Amazon Kinesis Data Analytics
- Amazon Kinesis Data Firehose
- AWS Lake Formation
- Amazon RDS
- Amazon Redshift
- Amazon Rekognition
- Amazon SageMaker
- AWS Step Function
- Amazon Textract
- Amazon Transcribe
- Amazon Translate
AWS-Role Metadata Information
| Type | Description |
|---|---|
| Role Name | Role Name, which uniquely identifies the functionality of the role. |
| Role Description | A brief explanation of the aws-role typically the functionality for what it is used. |
| Consolidated AWS Permissions | Permission is an action defined for a particular AWS service. Each aws-role consists of a group of permissions. These permissions determines the level of access within AWS. |
| UsersAttached | The list of users to whom the role is attached. |
| CreatedBy | Who created the role. |
| LastModifiedBy | Who has recently updated the role. |
| LastModifiedTime | Timestamp when the role was recently updated. |
Role Operations
If a users has sufficient permission they can perform the below operations on AWS-Roles.
| Functionality | Description |
|---|---|
| View Role | View existing Role Metadata Information. |
| Update Role | Update users attached on existing AWS-Roles. |
| Switch To Console | This functionality helps user to switch to AWS console using these AWS-Roles. |

The below gif shows Switch to Console feature.

Custom AWS Roles use case
An administrator wants to create a role with full read access to the DynamoDB service and assign this role to a set of users. The users who access the AWS console using this custom role will only have access to the DynamoDB service and will not be able to access other resources or perform other actions within AWS.
Step 1
The administrator will need to provide an IAM policy template in .txt file to the Amorphic team. This policy template should contain access to full dynamodb view permission. The Amorphic team will use this policy template to create the role in your AWS account.
Step 2
After receiving the IAM policy template, the Amorphic team will verify the policy to ensure it meets the user's needs and the security requirements. Once the policy is verified, the team will create the role in the user's Amorphic account.
Step 3
The administrator can view the newly created role and assign users to it through the Amorphic interface.
Step 4
Once a user has been assigned a role, they will be able to access the AWS console by selecting the "Switch to AWS Console" option under the profile section. The user will only have access to the resources and actions defined in the role's permissions.
Custom AWS Roles and Operations
The custom roles created through Amorphic are unique to the user's account and can be managed by the user's administrator. The user will have access to the resources and actions defined in the role's permissions and it is important to keep the permissions updated as per the requirement.
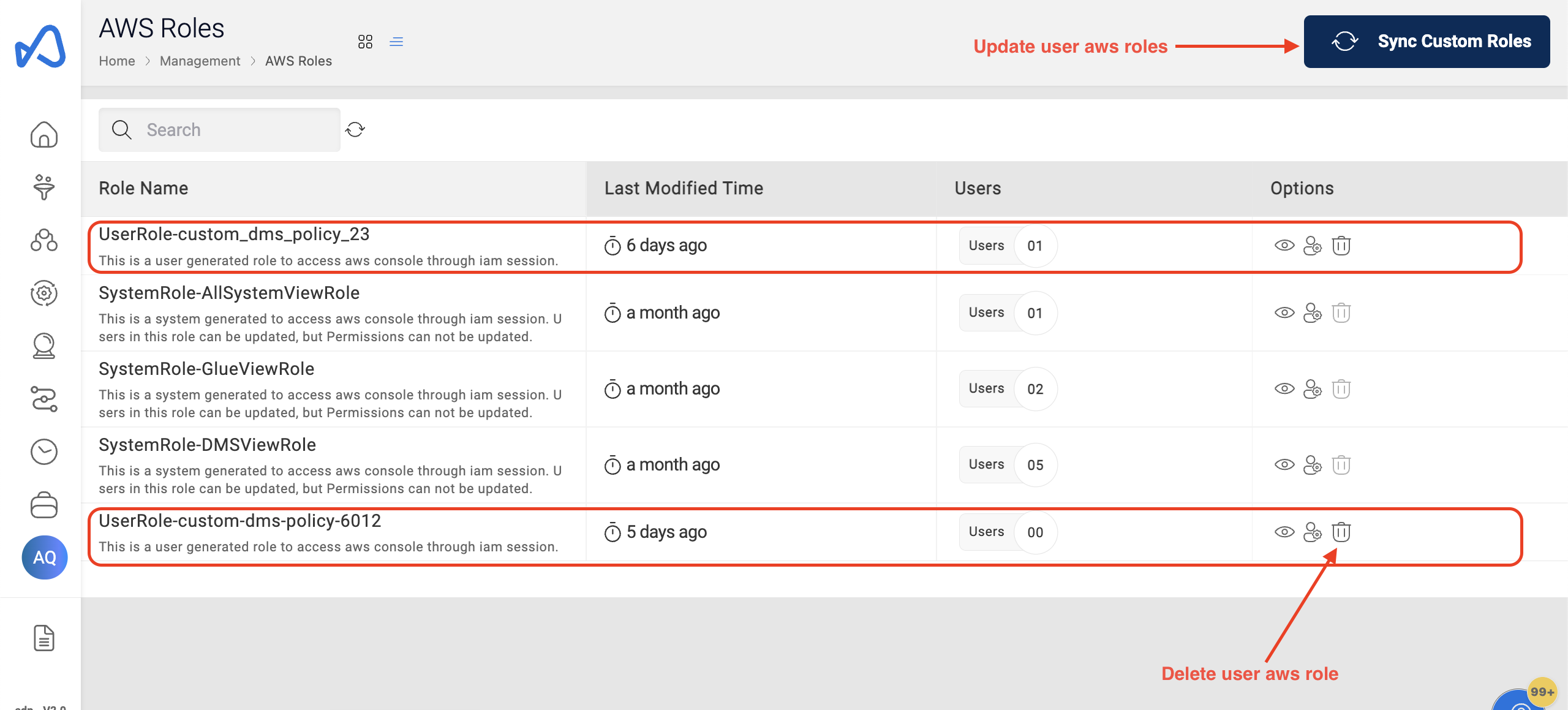
Sync Custom Roles Option
If the user wants to update the IAM permissions for a role, they will need to provide an updated policy document to the Amorphic team. Once the Amorphic team updates the policy document in S3, the user will need to click the "Sync Custom Roles" button to apply the updated permissions.